Risk Simulator Software Case Study: Real Option Model and KVA Application in US Navy Military Strategy
This article is published by China Science Software Network. If you have any questions, please contact us.
This case was completed by Lieutenant Cesar Rios, Dr. Tom Housel, and Professor Johnathan. Lieutenant Rios is the intelligence officer of the Third Expeditionary Force in San Diego, California. Dr. Tom Housel is a professor of information science and teaches at the Naval Postgraduate School (NPS) in Monterey, California. For this case, if you have any questions, please contact Dr. Housel ().
The US Navy has spent millions of dollars investing in information technology (IT) research to provide information warfare (IW) rapid response capabilities and intelligence gathering systems. In order for the government to get the most out of it, we need to use the appropriate assessment tools. This case study applies KVA (Knowledge Value-Added) and the real option model to the Naval Password Upgrade System (CCOP) in the intelligence gathering process. For this reason, the US government looks at the process of human resources and information transfer. The goal of this case is to establish a reasonable model for the IW system to aid the design budget. Models must provide targets for measurement to enable assessment of existing and future CCOP systems.
Challenge
The director of the Naval Operations Management Office set the fiscal year 2005 target to three: efficiency, metrics, and investment income. With this in mind, CCOP's project director Brian Prevo found it very difficult to allocate funds in 12 IW CCOP systems. Should there be equalization of funds for each project? Is there a project that requires the most funds to upgrade? What are the preferences of users? In order to properly plan the budget, Prevo must measure the investment income of each CCOP system. In addition, he must make the project meet the US Navy's supervision and reconnaissance (ISR) of global information. Prevo worked with researchers at the US Naval Postgraduate Institute and also worked to help Cesar Rios at the Naval Postgraduate School. When performing ISR tasks, Rios is responsible for the management and control of CCOP systems and other IW systems on various platforms (ships, aircraft). Rios is the leader of the entire team and an expert in this area. He worked with Dr. Housel and Dr. Mun to complete the research on the allocation of CCOP funds.
background
Information is critical in US security strategies. According to the US National Security Strategy (NSS), information is the first line of defense against threats from the enemy and terrorists. After the "9.11" incident, the US military realized that the information strategy proposed for the Cold War could not adapt to the complicated US homeland security issue of the new era. In order to synchronize US intelligence capabilities with changing security threats, the United States has taken the following steps:
Provide a comprehensive information alert for the United States and its allies.
Develop new information technologies to maintain information superiority.
Increase investment in future espionage capabilities.
Collect and analyze intelligence related to terrorists.
US intelligence activities cost $40 billion a year, and most of them are spent on ISR activities. The ISR is a system for collecting, processing, and walking information. ISR provides most of the information for decision makers and the military of national security strategies. The components of the ISR system range from digital cameras to billions of dollars. Some ISR projects collect information extensively, while others collect information specifically for specific weapons; some are “national†systems that provide information to government authorities, and some are “tactical†systems that provide commanders with battlefield information. There are three types of ISR: National Information Project (NIP), Military Joint Information Project (JMIP), and Tactical Information and Related Activities (TIARA).
Most of the military intelligence comes from the Defense Intelligence Agency (DIA), which handles HUMINT, MASINT, most of the DoD strategy, and long-term analysis conclusions; the National Security Agency (NSA) handles SIGINT; the National Bureau of Surveying and Mapping (NIMA) ) mainly handles IMINT. To some extent, the military intelligence system also includes: the Central Intelligence Agency (CIA), the State Department, the Department of Energy, the Ministry of Justice, and the Ministry of Finance.
Maritime ISR
The Navy’s road sign conversion in 2003 required the reorganization of the Maritime ISR to combine the DoD 5000 Series with the Joint Warfare concept. Our goal is to define a set of metrics that enable information users to access information in a timely, cost-effective and efficient manner. The Maritime ISR is at the heart of the Naval Operations System and is a core element in improving the speed and efficiency of operations. In the face of today's security threats, it is necessary to expand the coverage of the ISR so that the military has the same decision priorities as the NSS.
The Intelligence Collection Process (ICP) is a tactical approach to maritime ISR units (ships, aircraft, and other platforms) that complete information requests. Once the information claims are met, various disciplines and information technologies will be used together to search, acquire, process, and feed back the results to tactical users (eg, ship officers and attackers) and users at the national level (eg, NSA). Figure 1.1 shows the approximate process.
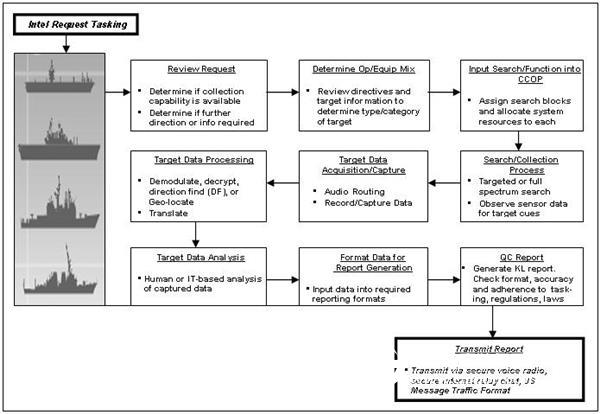
Figure 1.1 Intelligent collection process
Each process is further broken down into individual actions that may require a secondary process to be performed in the ICP. For example, the Target Data Processing can be broken down into the following tasks:
1. Artificial based (non-automatic)
a. Manually copy and report directly.
b. Manual translation and processing.
2. IT based
a. Direct conversion to report
(1) decoding
(a) All IT-based information.
(b) can be done manually.
(2) decryption
(a) All IT-based information.
(b) can be done manually.
b. Guide discovery
(1) Automatic - local orientation (LOB).
(2) Manual completion - LOB.
(3) Manual completion - B-rep requirements.
c. Geolocation
(1) Special treatment
Founded in 1994, CCOP has developed an intelligence system capable of responding quickly to information from land, sea and air. About 100 ships capable of deciphering passwords have entered the Navy. Each of them is a potential user of portable devices, underground and aerial platforms. The CCOP system has a wide range of functions, and its basic functions are as follows:
Tactical reconnaissance and positioning.
Passively guide, classify, and track enemy intent in the extended range.
Explain and report on the potential or known meaning of the intercepted data.
Relevance tracking.
CCOP is an advanced decryption system that leverages commercial off-the-shelf technology (COTS), government off-the-shelf technology (GOTS), modules, and open systems. When COTS and GOTS systems are applied to ISR systems, integration at various levels is required to provide conclusion reports and data analysis for systems and task managers. The COTS and GOTS systems need to be modified at certain levels to meet the needs of the ship. Before being put into actual operation, the system must undergo systematic testing to ensure practicality and reliability. They also need to be tested for cyber attacks (if they are connected to the Navy's network) and to test the ability to work together.
Evaluation technique
Investment in information assessment technology is a daunting challenge. Although we have many ways to evaluate investments in IT, return on investment (ROI) is still the most widely used to measure past, future, and potential accomplishments. Other techniques are used to assess the impact of IT at the corporate and sub-corporate levels of an organization. Although the methods are different, their goal is to provide management with a way to measure tangible IT investments and intangible intellectual assets. Company-level analysis can determine the performance of IT and intellectual assets within an organization. Subsidiary-level analysis looks at sub-processes related to organizational output and attempts to establish a set of metrics for measuring intellectual and IT assets within the secondary process.
ROI in the public domain
ROI can help managers and investors make effective decisions, but what if an organization does not produce measurable benefits like DoD in the US? Traditional ROI metrics do not measure the benefits of public sector IT systems. When using ROI analysis for the public sector, you need to pay attention to the following points:
The lack of effective criteria for measuring returns and profits poses a huge challenge in measuring the total revenue generated by the entire organization.
It's hard to find real data in a bunch of tricky data.
ROI relies on costs and benefits; it is difficult for us to distinguish between stakeholders and equity holders because potential stakeholders are project participants, participant managers, project sponsors, or taxpayers.
Regardless of obligations and costs, the government must provide services to society.
The public budget department is receiving increasing attention as equity holders, managers and taxpayers continue to place increasing demands on government obligations and the transparency of public investment. This has led to increased regulation, as in the Government Performance Act of 1993 (GPRA), which requires the establishment of standards for measuring strategic planning and performance for consideration of obligations and costs. These challenges force the public sector to find quantitative methods to measure the total value of public services and public goods.
ROI in the DoD project
Funding for many intelligence projects comes from DoD, which requires all IT projects to be managed as investments rather than gifts. To achieve this goal, meet government regulatory measures, and comply with GPRA, Information Technology Management and Performance Act (ITMRA) regulations, DoD must effectively measure the investment process. Although profitability is not the primary goal of DoD and non-profit organizations, the government must ensure that taxpayers' money is used effectively and that citizens and society receive the maximum benefit.
There are many problems when measuring total revenue and risk with ISR. The complexity of technology (which stems from the use of COT/GOTS systems, open building systems, evolving software standards, reduced time constraints, and instability of funding) poses a threat to maritime ISR systems. Although DoD implements rigorous testing and evaluation (T&E) on all projects and projects to reduce risk, there is still a lack of standards for accurate measurement of IT systems. The ability to develop measurable key performance parameters (KPP) and effectiveness metrics (MOE) to measure performance in a variety of environments determines the success or failure of T&E.
Another difficulty in this case is the conversion of output into monetary benefits. In the business case, the output is expressed as the price per unit, but for DoD and non-profit cases, such an approach does not work. This problem will arise when applying empirical financial analysis, especially when looking for the bottom line for making fiscal decisions. The assessment methodology adopted by DoD must include a common framework to understand, evaluate, and validate government influence on IT investments from a global perspective of US national security. For this purpose, the KVA method is a viable evaluation technique.
Intellectual value-adding methodology
The Intellectual Value Added Methodology (KVA) was created 15 years ago by Dr. Thomas Housel and Dr. Valery Kanevsky to assess the value added of intellectual assets (manpower and IT). The theory is based on the assumption that commercial organizations and all other organizations produce products (eg, physical goods and services) through a series of processes and sub-processes that convert raw inputs into output products. Process (for example, turning labor into services and turning information into reports). In the organization of production, changes in inputs occur just as entropy changes. In the American Traditional Dictionary, entropy is defined as "a measure of the changes that occur in a closed system." In the business world, entropy can be used to measure the degree of change in inputs in the process of obtaining output.
If we can describe the unit output of all processes, managers can measure costs and benefits at any point in time. At the sub-organizational level, we can measure access to information, traditional accounting, financial performance, and profitability. KVA has two important differences from other financial models: KVA can analyze metrics at the sub-organizational level; for accounting accounting, it can configure costs and benefits in all secondary processes.
Based on intellectual assets, KVA mainly controls the relationship between entropy and value appreciation. The units of change caused by the production process are measured by the intellectual assets required to cause these changes. More specifically, the average time required for workers to receive training is used to measure changes in entropy.
This case applies KVA, Monte Carlo simulations, and real option models to USS Readiness, so that we can see how project managers measure finances in the process and secondary processes of each CCOP system.
USS Readiness
The goal of this case is to assess the efficiency of the CCOP system in offshore ISR. Using the KVA approach, we can develop metrics and compare CCOP with existing and future projects. In this section, we will review how KVA can be applied to two secondary processes of the CCOP project: R&D/collection process (P4), data format, and report summary (P8).
USS Readiness is an imaginary US Navy ship performing ISR missions. In addition to the flight attendants, the ship also has an IW operator who uses the CCOP system to perform the intelligence gathering process; it is equipped with a regular supply that can last for six months and is responsible for daily ISR collection tasks at the national and tactical levels. The two teams on the USS Readiness (ISR and IW personnel) include: the divisional commander, the subordinate commander of the division, the signal operator, and the public operator. Each IW commander performs a special process in the ICP. Upon request, the ISR team member will provide a series of reports, including: reports of original intelligence, technical reports, communication between analysts, and daily summary reports. USS Readiness is equipped with 4 CCOP systems (A, B, C and D).
See Table 1.1. On a particular platform with infrastructure, the CCOP system can be applied to a single secondary process or a composite secondary process. In addition, some systems, such as the CCOP A system, are very complex and contain multiple secondary systems. With KVA, we can measure costs and benefits (see Table 1.2). Obviously, for a company, costs and benefits can be quickly obtained, but the real use of KVA is in the public domain.
Table 1.1 CCOP System Ready for USS
Secondary process name
CCOP A
CCOP B
CCOP C
CCOP D
P1
Return request/task
X
P2
Decision optimization/device combination
X
P3
Production function research/planning plan
X
P4
R&D/collection process
X
X
P5
Target data acquisition/capture
X
X
P6
Target data processing
X
X
X
X
P7
Target data analysis
X
X
X
P8
Data format and report summary
X
P9
QC report
X
P10
Delivery report
X
Table 1.2 P4 and P8 cost configurations for CCOP C, D and fixed IT infrastructure
Agency income assigned to CCOP C ($US)
Cost assigned to CCOP C ($US)
Agency income ($US) assigned to CCOP D
Cost assigned to CCOP D ($US)
Agency income assigned to a fixed facility ($US)
Cost assigned to a fixed facility ($US)
$-
$-
$28156
$10250
$-
$-
$13868
$10250
$58253
$12000
$19906
$63462
$241667
$102500
Table 1.3 lists the main results, where ROK is the intellectual income (productivity), ROKA is the income of intellectual assets (margin), and the return of ROKI intellectual investment (value equation).
Table 1.3 P4 and P8 KVA Matrix
Total KVA matrix
Secondary process name
ROK (proportion)
ROK (percentage)
ROKA
ROKA
P4
R&D/collection process
3.39
339.01%
70.50%
239.01%
P8
Data format and report summary
0.80
79.63%
-25.59%
-20.37%
Total matrix
14.10
1410.20%
157.31%
410.20%
KVA can provide structured data for different risk analysis and other analysis (such as real option analysis). Combining KVA's historical performance metrics, simulations, and real option models allows CCOP management and the US Navy to evaluate and compare the future value of human assets, systems, and options for configuration and hiring.
Analysis of the real option model
As shown in Figure 1.2, the real option model is used to determine the future value of the three basic options. The real option model with KVA data (this model has a step size of 8) was used to estimate the value of the options mentioned in this book.
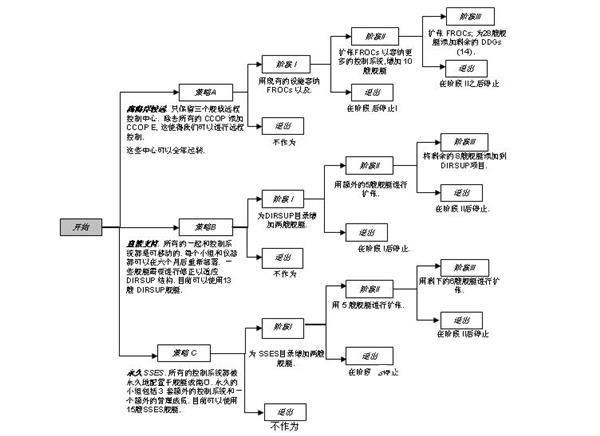
Figure 1.2 Three path-dependent real option strategies for CCOPs
The first option (A—away from the coast) uses a number of different CCOP systems that allow all generated data to be analyzed by remote monitoring centers. The reason for this is that the following considerations: If the intelligence gathering process can be completed by a remote unified monitoring center, then only fewer intelligence personnel need to be equipped on the ship. Now the military prefers this idea of ​​using a remote unified control center, because it can reduce expenses and improve shore-based combat capabilities. This is just like a unified customer service control center in the business world, such as a larger but smaller number of call centers.
The second option (B—direct support) looks at how to transfer CCOP equipment and operators between ships. The idea is that when a ship is docked for maintenance, repair or upgrade, we transfer the CCOP equipment and operators of the ship to the ship that is about to sail. In this way, the ship's intelligence collection requires fewer CCOP equipment and operators.
The third option (C-Permanent SSES) does not allow the transfer of CCOP equipment and operators on the ship. This approach requires more CCOP equipment and operators, which increases the potential cost, but provides ship commanders with more powerful intelligence control capabilities.
An analysis of these results (shown in Figure 1.3) shows that option C has the greatest value. This result will cause us to question, since both option B and option C can save costs, why are their values ​​not as good as option A? However, because KVA provides monetization metrics, this makes it possible for us to see options C has a higher return. The commander of the ship chooses option C because it provides greater control over intelligence assets. So instinctively, the commanders will choose option C, but without KVA, we can't provide a scientific basis for the commander's intuition.
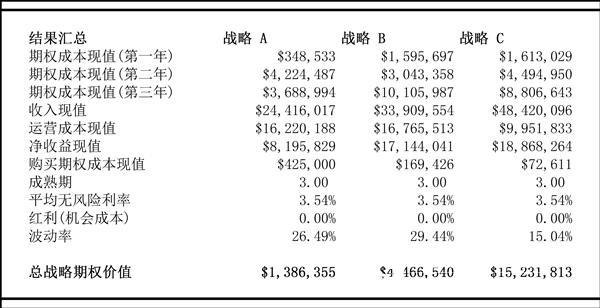
Figure 1.3 Summary of the results of real option analysis
As time and experience grow, remote options may offer higher unit cost benefits than data collection techniques, as remote control can provide more powerful operational control for ship platforms. However, the current bandwidth limitations of the naval operations control environment constrain the remote control system because the remote control system has high bandwidth requirements.
The CCOP project management requested further analysis using KVA and the real option model. The Navy battle group is currently assembling software that can use KVA, simulation, and real option models to monitor the data collection process and the performance of the CCOP system in real time. Next, we will enable the software to find the best options for the CCOP system configuration plan for commanders and project managers to meet the needs of naval commanders and other federal agencies involved in intelligence gathering and analysis.
Handheld Garment Steamer
Handheld Garment Steamer,Best Handheld Steamer,Handheld Steamer For Clothes,Hand Steamer For Clothes
NINGBO ZHONGJIA ELECTRICAL APPLIANCE CO., LTD. , https://www.foodzhongjia.com